Are Decentralized Identities the Future of CIAM?
Empower your users, build trust that lasts, and get enhanced security with DCI.
Decentralized identities (DCI) are gaining popularity as a potential solution to the problems that centralized identity management systems, such as federated identity, present. CIAM (Customer Identity and Access Management), a subset of identity and access management (IAM), controls the identities of customers rather than allowing employees or other types of users to manage account access. This contrasts with the traditional approach to identity management in which a centralized authority, such as a government or a company, holds and manages individuals’ identity information.
Integrating DCI may be the future of CIAM systems. Gartner’s newest Hype Cycle™ report for 2023 cites decentralized identities as a digital identity trend with “transformational” benefits that will plateau within 2-5 years.
Organizations that can implement DCI into their CIAM systems now will be able to empower their users to manage how their personal information is used, shared, and accessed – building trust that lasts, loyal customers, and returning business opportunities. Businesses will also benefit from enhanced security, better UX, and decreased costs associated with fraud losses, password resets, and more.
What is CIAM?
Your business may already use IAM to control internal employee access to networks, applications, and resources. While CIAM extends some of the functionality of an IAM solution to managing access for external customers and partners, its characteristics and use cases differ.
CIAM provides a way for organizations to safeguard accounts and data from unauthorized access by integrating authentication and authorization into customer applications. It enables businesses to securely capture and store customer identity data and control account access without creating additional customer friction. The core features of a CIAM solution include:
Security and privacy
CIAM solutions provide end-to-end security for customers and their accounts. They enable you to manage authentication mechanisms, encrypt data, define information download restrictions, receive alerts when risky activities occur, and gain a granular view for detecting unusual user and administrator behavior.
Scalability
Business growth means adding customers. But new customers may come one at a time or all in a rush in response to a campaign, trend, or other factors. No matter how new customers come, or how many there are, CIAM solutions should scale seamlessly to accommodate them without decreasing security or exposing accounts or data to risk.
Authentication
With CIAM solutions, you can adapt authentication to user preferences for a better experience, including MFA (multi-factor authentication) options to empower users when it comes to choosing how they authenticate themselves. You can offer SSO, FIDO authenticators, biometric authentication, one-time passcodes, sign-on using social media credentials, push notifications, email links, and more. Multi-factor authentication that combines two or more of these methods can be used to protect highly sensitive data and accounts that require extra security.
Integration
CIAM solutions integrate customer data from CRM, CMS, CDP, and other systems into a unified customer view. This view can include purchase history, customer identities, trends, and other details that help you personalize and deliver a consistent customer experience across all the channels and applications a customer uses to interact with your business.
What are decentralized identities?
A digital identity includes a body of information about an end user, organization, or electronic device that exists online. This information could be things like usernames and passwords, Social Security Numbers, search history, buying history, birth dates, addresses, phone numbers, and more.
Decentralized identity systems consist of an issuer, a holder, and a verifier. Holders may be, for example, universities, certificate and training programs, or passport departments; credential holders are the end users (your customer or employee); verifiers are the middle-entity (your organization), such as a financial institution, ecommerce site, or employer.
The holder presents proof of their identity to a verifier when a verifier requests it. DCI allow users to control and present their identities without relying on a specific third-party service provider. Unlike centralized identity management systems, decentralized identity solutions – like identity wallets and biometric factors – give the control back to the individual, providing a level of security and UX unmatched by legacy systems.
DCI also foster inclusion and accessibility for citizen services, like employment resources, healthcare, voting access, and more; by only requiring a smart device and an internet connection, decentralized identities are allowing more and more people around the world to access both life-affirming and necessary services.
Examples of DCI
Decentralized identities come in many forms, but what these different technologies have in common is that they consist of verifiable credentials (VCs) and decentralized identifiers (DIDs). According to Gartner, “Private keys and verifiable credentials (VCs) are contained in digital wallets, supported by an identity trust fabric for making DIDs discoverable.”
Digital wallets, or identity wallets, are the most common example of DCI. Instead of organizations constantly asking users to prove their identity for every service they wish to use or authenticate every time they wish to access an account, identity wallets contain all components of a user’s PII (personally identifiable information) and allow them to authenticate themselves across service providers, saving themselves time, providing greater security for all parties involved, and cutting costs for businesses when it comes to being able to phase out clunky, outdated identity security infrastructure.
Benefits of DCI as a CIAM strategy
Individuals have little control over their own identity information in a centralized digital identity management system. Some individuals in under-resourced areas may not even be eligible or able to establish an identity – digital or otherwise – through centralized systems; in fact, about 850 million people around the world do not have official documentation.
When a central authority controls this information, users have no insight (beyond the typical data privacy waivers, et al.) into how their PII is being used, where or how it’s being stored, and who or what can access it.
That’s a scary thought for most people, and yet that’s the condition upon which we share most of our data today. And for organizations, especially in a market that’s saturated with entities across industries relying on traditional identity management, it not only financially pays to make the investment into decentralized identities – it shows potential and returning customers that you care about their privacy.
An important advantage of decentralized identities is that they can reduce the risk of identity theft and fraud. An attacker who gains access to the central authority’s database in a centralized system can steal the identity information of thousands, if not millions, of people.
With DCI in place, however, a bad actor would have to gain access to each individual’s identity information separately in order to wreak any havoc – a feat which is much more difficult, if not impossible, especially on a larger scale.
There are also benefits for businesses that use decentralized identities. DCI can help to improve the customer experience by making it easier for users to access the services they require. They can also assist businesses in complying with privacy regulations, such as the General Data Protection Regulation (GDPR), by providing individuals with greater control over their identity information. DCI is a more customer-forward way of remaining compliant with privacy regulations, as reliance on decentralized user data is superior to traditional methods.
DCI allow businesses to instantly verify a customer’s identity, giving them the confidence they need to enact secure transactions while knowing the user has provided virtually fraud-proof credentials.
What to keep in mind when implementing DCI
Enterprise security and risk managers should prioritize the following key strategies when implementing CIAM or decentralized identities:
- Facilitate the proper integration of the CIAM or decentralized identity system with the organization’s existing systems and processes by working closely with IT staff and other stakeholders to ensure that the new system is compatible and does not introduce any new security vulnerabilities.
- Create and deploy strong access controls and authentication mechanisms to ensure that only authorized individuals have access to sensitive data and systems. This may entail implementing two-factor authentication, role-based access controls, and other security measures.
- Conduct regular security assessments and penetration testing to identify potential security gaps and vulnerabilities. This can aid in ensuring the security and resilience of the CIAM or decentralized identity system.
- Regularly train and educate employees on the use and security of the CIAM or decentralized identity system to reduce the possibility of employees unintentionally exposing the organization to security risks through their actions.
- Design and implement a robust incident response plan to react to security incidents quickly and effectively. This should include steps like determining the cause of the incident, containing the damage, and restoring systems and data to their normal state.
It’s best to focus on developing and implementing a comprehensive, integrated security strategy that addresses the unique challenges and risks posed by CIAM and decentralized identities, as well as on monitoring and updating that strategy on a regular basis to ensure its effectiveness.
Potential difficulties with DCI integration
There are some potential drawbacks to adopting decentralized identities. For example, there is currently no widely accepted standard for decentralized identities, which means that different systems may be incompatible. This can make integrating decentralized identities into existing systems difficult for businesses.
Another challenge is the general public’s lack of awareness and understanding of decentralized identities. Many people may need to be educated about decentralized identities and the potential benefits they can provide. This can make it difficult for organizations to persuade people to use decentralized identities.
How we can help
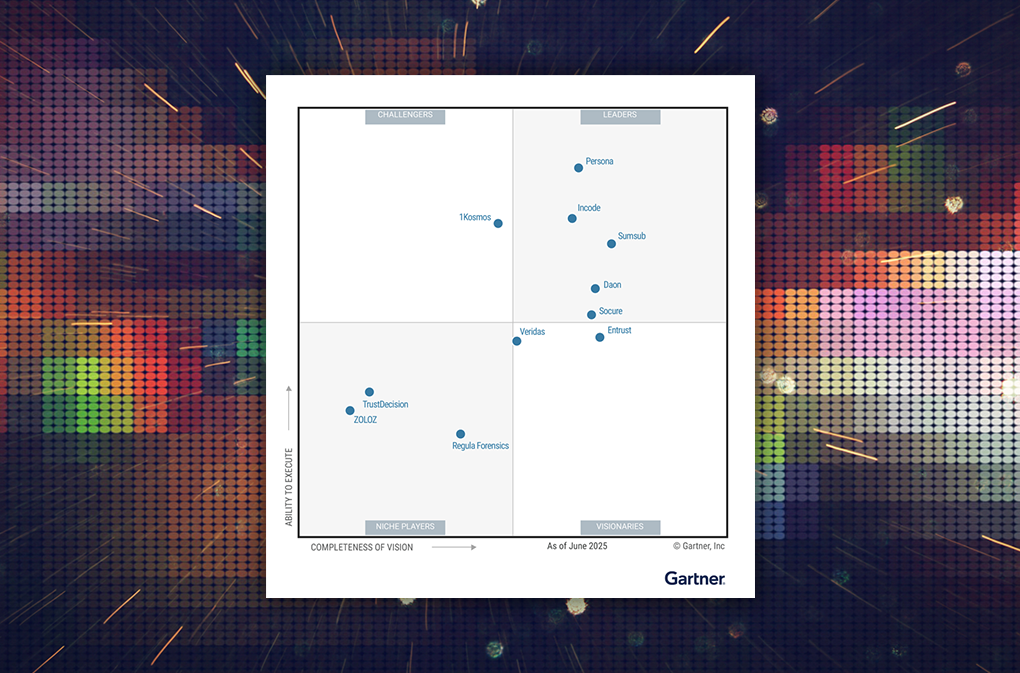
While DCI have many benefits, they also face significant barriers to adoption. Daon’s team of solutions experts and engineers believes in placing the individual human back at the center of digital identity. This goal fuels our over 20 years of experience with innovative identity technologies, biometrics, and CIAM. Check us out in Gartner’s most recent report here to learn more about how we can help futureproof your business with decentralized identities.