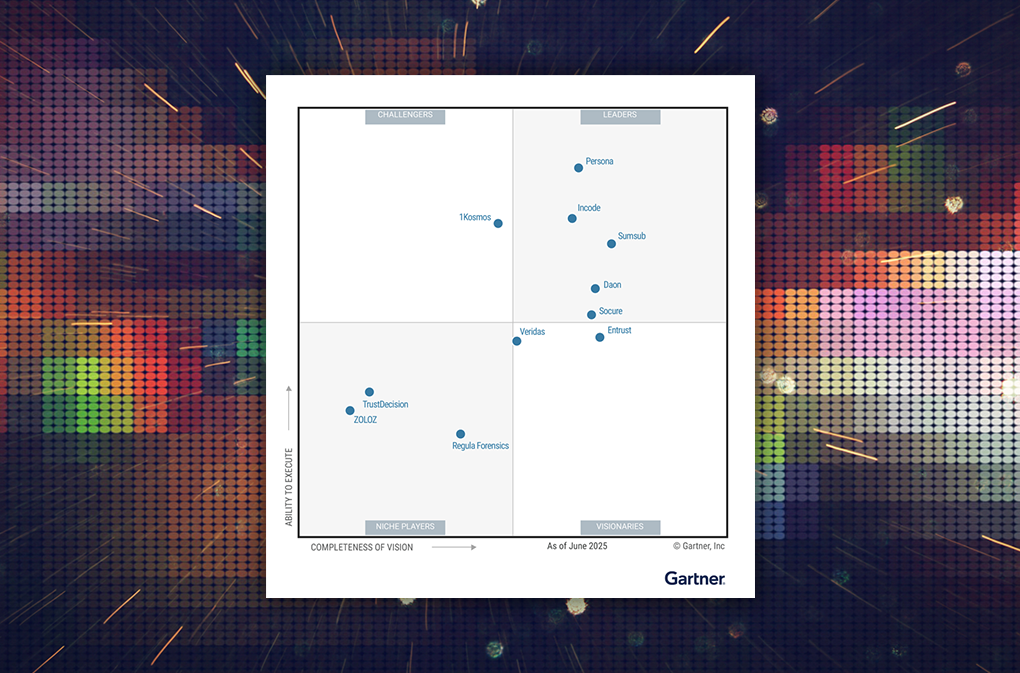
Invisible Authentication
Explore the most common frictionless multi-factor authentication methods and their benefits
by Ralph Rodriguez, CPO
January 17, 2023
Frictionless, or “invisible,” MFA is an authentication process that uses multiple factors to verify a user’s identity. Invisible MFA is designed to reduce the amount of effort required by users when authenticating themselves. It uses various factors, such as device recognition, geolocation data, and physical and behavioral biometrics, to authenticate the user without requiring them to enter additional information. By using invisible MFA, organizations can ensure that their customers have a secure and convenient user experience while protecting their data and the privacy of their customers.
But…what makes this method invisible, exactly? Designed to be as seamless for the user as possible, invisible MFA aims to provide the same level of security as traditional (legacy) MFA methods, all without requiring the user to take any extra steps. With invisible MFA solutions, the authenticating party does not “see” any part of the authentication process unfolding. The user can “come as they are” and utilize factors they already possess, like their face, their location, or their device, to authenticate their identity.
Depending on the use case, invisible MFA factors will be more or less successful for a given user and for the organization implementing the authentication process. Keep reading to learn about the different types of frictionless MFA methods and the situations where they can be used.
Frictionless MFA techniques
Below are some of the most common factors used for invisible authentication. Each comes with its own set of parameters, pros, and cons.
Device-based authentication
This method allows the user’s device, such as a computer or smartphone, to be used as an authentication factor to access their account. The device is linked to the account and can authenticate the user without any additional information.
Pros: Using device recognition can prevent unauthorized account access because it is difficult for an online attacker to obtain and use a registered device.
Cons: This method may not be as secure as other MFA techniques because it relies on the device’s security. If the device is compromised (via malware or a physical attack, for example), an attacker could potentially use it to circumvent MFA.
Location-based authentication
Location-based authentication utilizes the location of the device being used to access the account as an authentication factor. The user can authenticate if the device is in a known, trusted location, such as the user’s home or office.
Pros: As it is difficult for an attacker to access a trusted location, this method can also be effective at preventing unauthorized access.
Cons: This technique may not be as secure as other MFA methods due to its reliance on accurate location information. If location information can be manipulated (via spoofing or other means), an attacker may be able to circumvent MFA.
Biometric authentication
Here, the user’s unique biometric characteristics (such as their fingerprint, voice, or face) are used as an authentication factor.
Pros: Biometric features are difficult to forge or steal, making this a highly secure method. It’s also impossible for a user to lose or forget their biometric characteristics – the user themself is the password!
Cons: This method may not be suitable for all users, however, as some may not possess the required biometric characteristics (e.g., due to physical disabilities or other factors). In addition, biometric authentication systems can occasionally generate false positives or false negatives, resulting in incorrect denial or granting of access to users.
While no MFA technique is foolproof, and different methods may be more or less appropriate for different situations, invisible MFA provides higher security and a better user experience than legacy MFA methods. When choosing authentication solutions, it’s always vital to weigh the benefits and drawbacks of each approach and select the one that best meets your organization’s or system’s needs and requirements.
Face, Finger, or Voice?
There is frequent debate about whether face, finger, or voice biometrics is the most effective MFA factor. Face biometrics are becoming increasingly popular as they are more user-friendly and require minimal effort from the authenticating party. Face recognition is also considered one of the most secure forms of authentication, though it can be relatively slow when compared to fingerprint or voice. Finger biometrics also provides a high level of security. It’s fast and convenient but may only work well in certain environments or with certain users, due to factors such as dry or wet skin or dirt on the finger surface. With advances in AI/machine learning technology, voice recognition is becoming more reliable but can be vulnerable to spoofing attacks if not implemented properly. Using voice recognition can also be problematic in noisy environments if multiple people speak simultaneously.
It is difficult to determine which type of biometric authentication is “best” because the suitability of a particular biometric technique depends on several variables. The following are some things to consider when selecting a biometric authentication method.
Accuracy
Biometric techniques have varying degrees of accuracy, with some being more susceptible to false positives or false negatives. For instance, fingerprint recognition may be more accurate than facial recognition but less user-friendly.
Convenience
Some biometric techniques may be more convenient than others for users. Voice recognition may be more convenient than fingerprint recognition because users can say a phrase instead of touching a sensor.
Compatibility
Different biometric techniques may or may not be compatible with specific devices and systems. Facial recognition may be more prevalent on mobile devices, whereas fingerprint recognition may be more prevalent on laptops.
Security
Biometric techniques offer different degrees of security, with some being more difficult to forge or steal than others. As it is easier to obtain a clear image of someone’s face than of their iris, facial recognition may be less secure than iris recognition.
Giving your customers options when it comes to selecting an MFA method – meaning your customer may choose which factor they’d like to use to authenticate themselves – may be an excellent solution for both user experience and enhanced security. Plus, you are on the road to building lasting trust and brand loyalty by empowering your customers to take control of the authentication process.
Should Biometric MFA Be Used Alongside FIDO2 or FIDO UAF?
FIDO (Fast IDentity Online) is a set of open authentication standards that can be used to enhance the security of online accounts and services. FIDO2 and FIDO UAF (Universal Authentication Framework) are standards within the FIDO framework that can enable biometric multi-factor authentication.
Incorporating biometric MFA into a FIDO2 or FIDO UAF system can provide users with a convenient and secure way to authenticate themselves, enabling them to use biometric characteristics (such as their fingerprint or face) as one of the authentication factors. It is difficult for an attacker to forge or steal a user’s biometric characteristics, which can help prevent unauthorized access to accounts and systems.
Using FIDO2 or FIDO UAF in conjunction with biometric MFA can be a valuable way to increase the security of your system. Still, it should not be relied on as the only authentication method. When deciding whether to use FIDO2 or FIDO UAF in conjunction with biometric MFA, combining multiple MFA techniques is generally recommended to provide the highest level of security.
Pros and Cons of FIDO2 and FIDO UAF
The FIDO framework enables passwordless, secure authentication. Here are the potential advantages and disadvantages of each standard.
FIDO2
FIDO2 is a recent standard, designed to be more flexible and interoperable than earlier FIDO standards. It supports a variety of authentication techniques, such as biometric techniques and hardware tokens. In addition, FIDO2 is compatible with online and offline authentication and a vast array of devices and platforms. As a result of its use of public key cryptography, implementing FIDO2 may necessitate more significant technical expertise and infrastructure than other FIDO standards. It may also be more difficult for users to employ, as a separate authentication device is required (such as a hardware token or smartphone).
FIDO UAF
FIDO UAF is designed to be lighter and more user-friendly than other FIDO specifications. It is easily integrated with various devices and platforms and supports a variety of authentication techniques, including biometrics. Since it does not support hardware tokens or public key cryptography, FIDO UAF may not provide security as robust as other FIDO standards. It is also restricted to online authentication and may not be applicable in disconnected or offline environments.
When deciding which FIDO standard to implement, you should keep your organization’s requirements for security, flexibility, interoperability, and user experience in mind.
MFA in 2023 and Beyond
Many different aspects of the enterprise will influence the future development and use of multi-factor authentication. Though it’s difficult to make precise forecasts, the following trends may impact MFA in the coming years:
Continued acceptance of biometric MFA
Biometric MFA techniques, such as face, voice, and fingerprint recognition, will most likely continue to gain popularity as practical and secure methods for authenticating users. These strategies can be implemented in a range of devices and systems, such as smartphones, laptops, and other types of technology, like software-defined vehicles (SDVs).
Increased usage of FIDO standards
The adoption of FIDO standards like FIDO2 and FIDO UAF to enable passwordless, secure authentication is projected to increase. These standards offer a wide variety of authentication approaches, such as biometric techniques and hardware tokens, and can be easily implemented into multiple devices and systems.
As MFA gets more generally implemented, a greater emphasis will be placed on making the authentication process as seamless and painless as possible for users. This may involve the use of invisible MFA techniques.
IdentityX® lets you pick your own plug-and-play modalities and algorithms to create an intelligent, layered authentication journey for your customers. To learn more about making your MFA invisible, get a free demo today.